The Toxic Cloud Triad: A Critical Risk You Can’t Ignore — Tenable’s Cloud Security Guide
Cybersecurity is evolving fast, and Tenable’s Cloud Risk Report 2024 warns of a rising threat — the toxic cloud triad. This toxic combination of cloud workload exposure, IAM vulnerabilities, and excessive permissions heightens the risk of cloud breaches more likely than ever.
In 2023, over 95% of cloud breaches were due to exposed or mismanaged workloads. This shows how big of a risk it is for companies today1.
Key Takeaways
Tenable highlights the need to tackle the ‘toxic cloud triad’ for better cloud security.
It’s important to understand how workloads, IAM issues, and too many permissions add up.
The Cloud Risk Report 2024 is a key tool for spotting threats in the cloud.
Companies should create strong plans to prevent cloud breaches.
Using a complete approach to cloud security can handle today’s complex cyber threats.
Being proactive in risk assessment and managing vulnerabilities is key to protecting cloud systems.
Improving cybersecurity knowledge and practices is crucial, as Tenable shows.
Affiliate Disclosure: This article contains affiliate links, which help support our work at no extra cost to you if you make a purchase through them. We only recommend tools like Tenable that we believe bring great value to our readers.
Understanding the Toxic Cloud Triad and Tenable’s Role in Securing Workloads
The toxic cloud triad is a key area in cloud security. It includes three main risks: too many permissions, weak cloud identities, and exposure to quick-fix vulnerabilities. A big 38% of global companies face high risks because of these issues2.
Tenable is a top name in fighting these cybersecurity risks. They help find and fix vulnerabilities in cloud workloads. The Tenable Cloud Risk Report shows 80% of cloud workloads still have unfixed critical vulnerabilities2.
To tackle risky access keys in 84% of companies and too many permissions in 23% of cloud identities, Tenable offers advanced tools. These tools help spot and fix these problems2. The report also points out that managing these cloud vulnerabilities is hard, even though they’re very important3.
Also, the rise of containers, like Kubernetes, adds more complexity and security risks. With 41% of security teams missing the right skills, there’s a big need for experts and good strategies to keep these environments safe23.
In short, dealing with the toxic cloud triad and managing vulnerabilities well is crucial. By using Tenable’s smart solutions and following good security practices, companies can better protect themselves from cyber threats.
Identifying Critical Exposures in Cloud Workloads
The cloud is now a key part of IT infrastructure, powering applications and data storage. However, it brings along significant security risks, including critical exposures and compromised privileges in cloud workloads.
These critical exposures — such as workloads left publicly accessible or unpatched vulnerabilities — are central elements of the toxic cloud triad, as identified in Tenable’s Cloud Risk Report. This combination of exposures, unpatched flaws, and excessive privileges increases the risk of unauthorized access and data breaches.
By understanding and addressing one-day vulnerabilities — vulnerabilities that attackers exploit as soon as they become known — organizations can stay ahead of malicious actors. These vulnerabilities, often found in cloud workloads, are core contributors to the toxic cloud triad. They provide attackers with easy entry points if not swiftly mitigated.
A breach can happen any time — are you prepared? Take control today with Tenable’s solutions and safeguard your cloud.
How One-Day Vulnerabilities Threaten Cloud Workloads
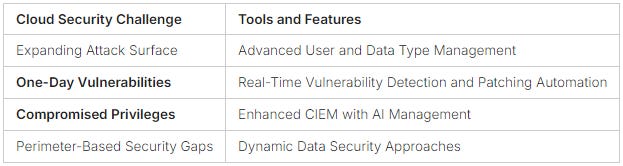
One-day vulnerabilities are a growing threat in cloud workloads. Attackers quickly exploit these gaps before they’re fixed. The cloud’s growing attack surface, due to more users and data types, makes this problem worse. Traditional security methods, based on old ideas, can’t keep up with the cloud’s fast-changing nature4.
Implications of Compromised Workload Privileges
When cloud workload privileges are compromised, the risks are huge. It lets unauthorized access and changes to data. This can lead to big data breaches. Tenable Cloud Security uses tools like Cloud Infrastructure Entitlement Management (CIEM) with AI to better manage data access4.
By closely watching and managing these areas, companies can strengthen their defenses against major vulnerabilities. This ensures strong IT security in their cloud workloads.
The Role of IAM and Credential Vulnerabilities in Cloud Security
Securing cloud infrastructures is crucial today. Understanding IAM and credential vulnerabilities is key for strong network security. A recent survey by the Identity Defined Security Alliance found that 84% of companies faced an identity-related security breach in a year5.
The Importance of Asset Discovery and Inventory
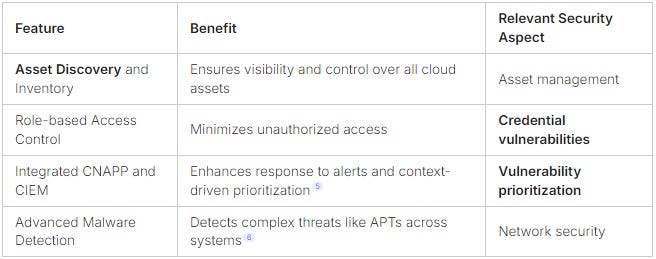
Effective asset discovery and management are vital for cloud security. By identifying all assets, organizations can apply the principle of least privilege. This ensures permissions are aligned with specific roles, reducing unauthorized access and enhancing security.
Tools like Cloud Infrastructure Entitlement Management (CIEM) and Cloud Native Application Protection Platforms (CNAPP) help achieve this. They provide comprehensive visibility, making network security stronger5.
Assessing and Prioritizing Vulnerabilities
It’s important to know which vulnerabilities to tackle first. Integrated security solutions, combining CNAPP and CIEM, make this easier. They help prioritize vulnerabilities based on their criticality and associated privileges, focusing on the most significant threats first5.
Malware detection, as seen in Tenable Cloud Security’s recent upgrades, also plays a role. It detects and assesses the risk posed by files across various operating systems and cloud services like AWS, Azure, and GCP6.
By focusing on asset discovery, IAM, and credential management, and using advanced security tools, organizations can strengthen their cloud environments. This strategic approach is key for robust vulnerability prioritization and network security, protecting vital digital assets.
Discover how Tenable can help you combat cloud vulnerabilities. Get started with a demo today and secure your cloud before it’s too late.
Combatting the Prevalence of Excessive Permissions
In today’s cloud-driven environments, managing access permissions is crucial. Excessive permissions have become a big problem. They make risk assessment, identity systems, and data protection very important.
When permissions are not controlled well, it leads to big security issues. This makes following rules and keeping data safe very hard.
Studies show that 99% of cloud identities have too many permissions7. To fix this, using IAM with least privilege and zero trust is key7. This way, only the right people can access what they need, keeping data safe.
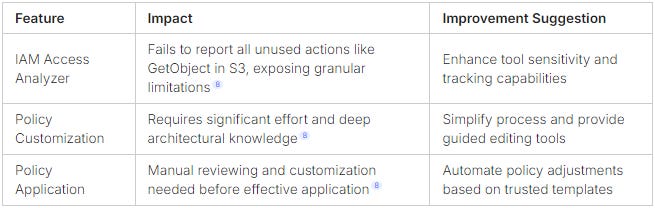
Improving IAM policies is hard, especially with tools like AWS IAM Access Analyzer8. These tools don’t always get the complexity of each action right. They need to get better to meet today’s cloud needs.
To keep data safe, encrypt it when it moves and when it’s stored7. Use strong encryption to stop hackers. Working with trusted cloud providers helps a lot too7.
Check user access often and watch privileged accounts closely7. This keeps your data safe and your system secure. Try to make your cloud setup simpler and automate policies when you can7.
In short, fighting excessive permissions is key to strong security and following rules. With the right strategies and tools, your company can stay safe from digital threats.
Managing Cloud Vulnerabilities with an Integrated Approach
As more businesses use cloud technologies, protecting them from threats becomes more urgent. A unified strategy not only boosts security but also covers all types of cloud threats. This is crucial for today’s complex cloud environments.
Unified Cloud and Kubernetes Security Management
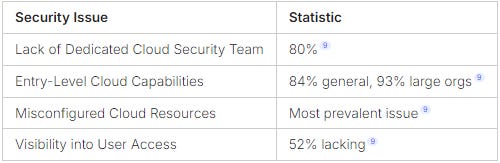
Managing cloud threats well means understanding threats and using strong Kubernetes security. Sadly, 80% of companies lack a team focused on cloud security9. This lack of focus makes them vulnerable to common mistakes, like misconfigurations, which are a big problem9.
For Kubernetes security, having a system that works well with your cloud is key. Tenable Cloud Security does this, offering cloud security management and Kubernetes protection10.
Cloud threats need quick scanning and fixing. A unified system helps by giving real-time insights and quick actions. This reduces risk a lot.
Statistics show that 84% of companies have basic cloud skills, with 93% of big ones too9. Without better security, they face big threats.
To improve cloud security, use integrated tools like Tenable Cloud Security. It not only protects but also shows you everything in your cloud. Also, managing who can access what is key, as 52% of companies struggle with this9.
An integrated approach to cloud security makes your systems safer. It helps you quickly handle new challenges. With tools like Tenable Cloud Security, you can make your cloud safer10.
Protecting your cloud is vital for your IT. Use advanced security and stay vigilant. An integrated strategy that fits with Kubernetes and cloud security is the best way to defend against threats.
Addressing Cloud Storage Risks and Sensitive Data Protection
The digital world is changing fast, making cloud storage security and data protection key issues. We must be careful to protect customer info and business secrets from cloud risks.
Securing Customer Information and Business Intellectual Property
With 74% of companies facing cloud storage issues11, keeping customer data safe is crucial. These problems let hackers in, risking data and trust. A big breach, like SolarWinds, cost the U.S. over $750 million to fix12.
Companies must protect their business secrets well. They need strong security to fight off attacks. A big breach at AWS showed how important it is to keep data safe12.
Cloud-Native Applications and Their Security Implications
Cloud-native apps are efficient but have security risks. Over 100 million users were hit in one breach12. We need a solid plan to keep these apps secure.
Using tools like Tenable One helps manage security across different clouds. It finds problems and fixes them fast, keeping data safe13.
Knowing the causes of cloud risks and how to protect data is key. Keeping customer info and business secrets safe needs a strong, proactive security plan. This is essential in today’s cyber world.
Tenable’s Expertise in Cloud Workload Risk Assessment
In today’s digital world, cloud breaches can cause huge damage. This shows we need strong ways to manage vulnerabilities. Tenable’s skills in cloud risk are key for keeping cloud environments safe.
Linking risk assessment, Tenable’s knowledge, and good vulnerability management boosts data safety. It also helps companies deal with new cloud risks better. With 80% of breaches hitting cloud data14 and costs over $5 million15, we really need strong protection.
Prioritizing Risks in Cloud Infrastructure
It’s crucial to focus on cloud infrastructure risks. Tenable’s tools help find vulnerabilities early. Shockingly, 95% of people have seen cloud breaches in 18 months14. Another study also found this15. This shows we must act fast to protect against high-risk vulnerabilities.
Strategies for Cloud Vulnerability Management
Managing cloud vulnerabilities also means understanding cloud complexities. Almost 60% of people said data leaks hurt a lot14. This shows we need strong data protection to avoid big financial and operational losses.
Tenable’s Cloud Security offers many features like constant vulnerability management and misconfiguration detection. It helps protect against data theft and leaks. It also helps businesses manage cloud risks better. In short, using Tenable’s expertise and good vulnerability management is key for strong risk assessment and cloud security.
Adopting Best Practices for Cloud Security Through Tenable’s Insights
Protecting cloud security is now more important than ever. Tenable’s insights help businesses strengthen their defenses against cloud breaches. They use strategies like Just-In-Time (JIT) controls and understand cloud infrastructure well. This way, they can manage and reduce risks effectively16.
Strategies to Protect Against Cloud Breaches
Tenable Cloud Security analyzes cloud resources continuously. It finds risks and gives insights for quick actions to protect against threats17. With 82% of breaches in cloud environments, strong security is key to protect data18.
Using just-in-time access and least privilege policies helps reduce attack surfaces. Tenable’s CNAPP and JIT for SaaS applications offer proactive security16.
Implementing Data Security Posture Management (DSPM)
Data Security Posture Management (DSPM) is crucial for cloud security. It helps prioritize risks based on data types and locations17. DSPM gives a detailed view of data landscapes, ensuring compliance and security.
Tenable’s approach fits well into DevOps workflows for continuous security checks. It simplifies security management across cloud providers like AWS, Azure, and GCP17. By integrating security into DevOps, Tenable secures development stages and ensures security in every cloud layer.
Tenable’s insights and cloud security solutions are essential for implementing DSPM and cloud security best practices. With comprehensive analytics and real-time monitoring, businesses can proactively address vulnerabilities. This keeps their cloud environments secure.
The Toxic Cloud Triad won’t wait — Secure your cloud with Tenable today and stay ahead of every threat.
Conclusion
Cloud security can no longer be overlooked. Tenable’s Cloud Risk Report 2024 identifies the toxic cloud triad as a pressing, but manageable threat. This real risk demands immediate attention.
With over 25,000 new CVEs reported in the past year19 and even more expected in 202420, organizations must act swiftly. Managing vulnerabilities isn’t just a best practice — it’s essential.
Tenable’s cybersecurity solutions offer fast detection and an extensive, up-to-date vulnerability database19. With frequent updates — often faster than the NVD — Tenable provides real-time insights to guide critical decisions.
To enhance cloud security, Tenable’s Exposure Response tools help organizations set actionable goals and manage risks effectively. By following these insights, companies can stay ahead of evolving threats.
Take control of your cloud security today. With Tenable’s insights and tools, you can stay ahead of evolving threats, protect your assets, and ensure seamless operations — because in today’s world, proactive security is the key to survival.
FAQ
What is the toxic cloud triad and how does it affect cybersecurity?
The toxic cloud triad is a set of big security problems in cloud systems. It includes cloud workload exposure, IAM and credential weaknesses, and too many permissions. These issues can cause serious security breaches and let unauthorized people access sensitive data.
How does Tenable help organizations in managing cloud workloads and their security?
Tenable offers risk checks, compliance tools, and ways to manage vulnerabilities. They help find and stop cyber attacks. With Tenable’s help, companies can better protect their IT systems from threats.
What are “one-day vulnerabilities,” and what implication do they hold for cloud workloads?
One-day vulnerabilities are new security flaws that affect cloud systems. They are a big problem because they can cause big breaches. It’s important to keep finding and fixing these issues to protect cloud systems.
Why is asset discovery and inventory vital in addressing IAM and credential vulnerabilities?
Finding and managing assets is key to stopping unauthorized access and identity issues in the cloud. It helps companies know where to focus on fixing vulnerabilities. This way, they can avoid breaches and improve their cloud security.
What challenges are associated with excessive permissions in cloud infrastructures, and how can they be mitigated?
Too many permissions can lead to big problems like data breaches. It’s important to carefully check permissions and set rules to balance needs and risks. This helps keep cloud data safe from unauthorized access.
How does an integrated approach to cloud security, including Kubernetes, benefit organizations?
A unified cloud security plan covers all parts of cloud systems, like Kubernetes. Tenable’s knowledge helps companies manage risks and protect important data from cyber threats.
Source Links
Harden Your Cloud Security Posture by Protecting Your Cloud Data and AI Resources
Tenable Bolsters Its Cloud Security Arsenal with Malware Detection
Managing Cloud Security: How to Avoid Common Misconfiguration Errors
Unused Access Analyzer: A Leap Toward Least Privilege, Not the End of the Journey
Cloud Workload Protection: The Key to Decreasing Cloud Security Risks
Improving Your Cloud Security Using JIT Access for Sensitive SaaS Applications
Study: Tenable Offers Fastest, Broadest Coverage of CISA’s KEV Catalog
Turning Data into Action: Intelligence-Driven Vulnerability Management